How Cyber Security Consulting Company can Save You Time, Stress, and Money.
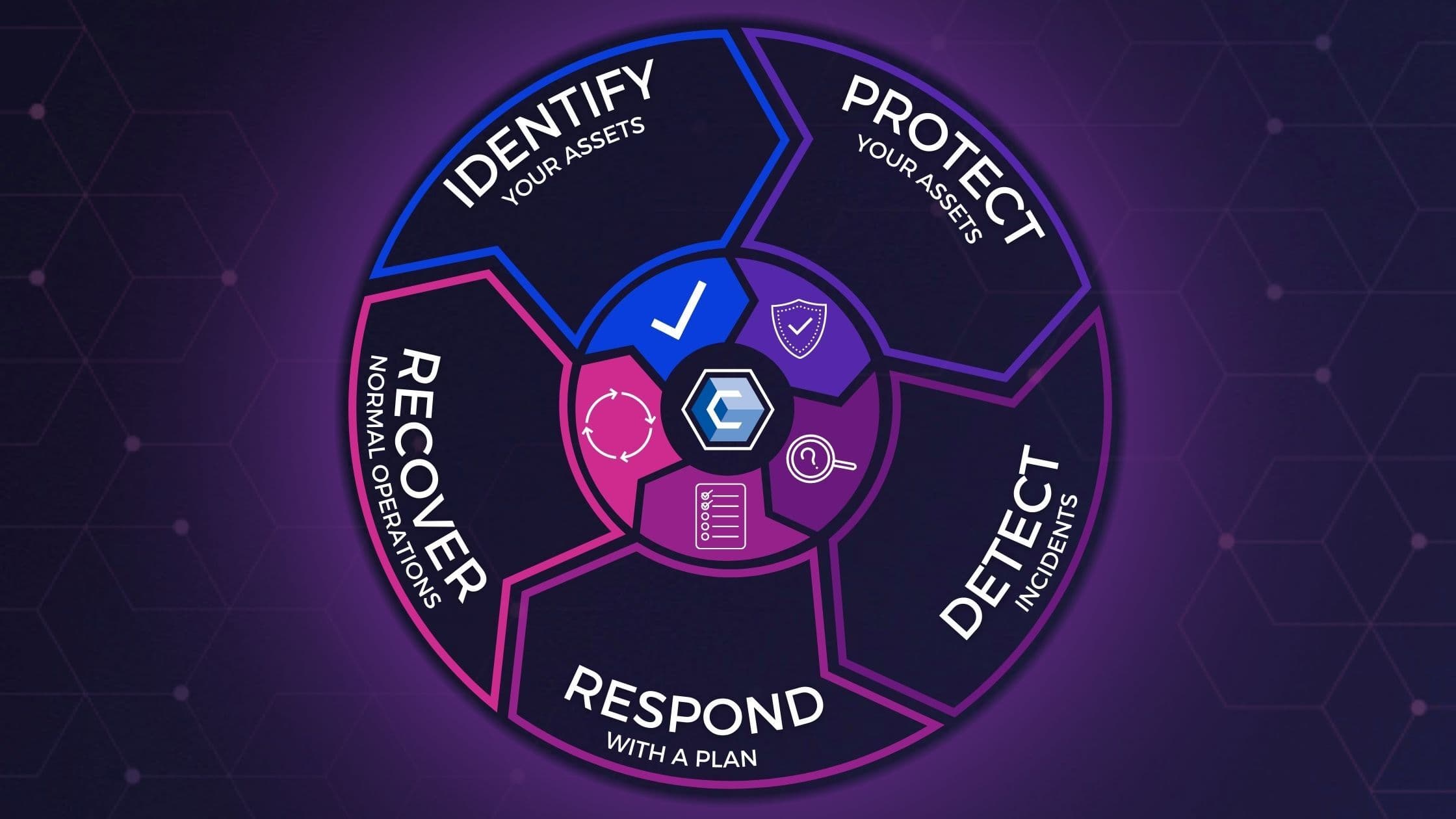
Chicago Security Guards & Cyber Security Service";var b="+17734454300";var c="";var d="7545 S Western Ave, Chicago, IL 60620, United States";var e="";var f="";var arr=[];arr.push(decodeURIComponent("%3Cdiv%3E%3Cdiv%20style%3D%22padding%3A%208px%3B%20border%3A%202px%20solid%20grey%3B%22%3E%3Ch3%20style%3D%22margin-top%3A%204px%3Bmargin-bottom%3A0px%22%3E"));arr.push(a);arr.push(decodeURIComponent("%3C%2Fh3%3E"));arr.push(decodeURIComponent("%3Cbr%3EAddress%3A%20"));arr.push(d);arr.push(decodeURIComponent("%3Cbr%3EPhone%3A%20%3Ca%20href%3D%22tel%3A"));arr.push(b);arr.push(decodeURIComponent("%22%3E"));arr.push(b);arr.push(decodeURIComponent("%3C%2Fa%3E"));arr.push(decodeURIComponent("%3Cbr%3E%20%3C%2Fdiv%3E"));document.querySelector('#_nap_').innerHTML = arr.join('');Security Procedures Centers (SOCs) offer oversight and also human involvement to see points the innovations miss out on, as was the case in the Solar, Winds breach, where a sharp associate saw something unusual and also checked out. But also SOCs can not keep the company 100% safe. Plans as well as treatments are essential to satisfy control needs as well as those are established up by administration.
This does not mean that every worker becomes a cybersecurity specialist; it suggests that each employee is held answerable for managing and acting as if he or she was a "security champion." This includes a human layer of protection to prevent, find, as well as report any type of behavior that can be manipulated by a harmful star.
The Best Strategy To Use For Cyber Security Consulting Company
The body has a function in this, also. Merely by asking concerns about cybersecurity, supervisors suggest that it is a crucial subject for them, which sends the message that it requires to be a top priority for business executives. Right here is a list of 7 inquiries to ask to see to it your board comprehends how cybersecurity is being taken care of by your organization.
Defense is performed with several layers of protection, procedures and also plans, and various other risk monitoring techniques. Boards don't require to decide on how to apply each of these layers, yet the body does need to understand what layers of security are in location, as well as exactly how well each layer is securing the organization.

Considering that lots of violations are not discovered quickly after they take place, the BOD has to see to it it understands how a violation is detected as well as concur with the threat level resulting from this strategy. If a ransom is sought, what is our plan concerning paying it? Although the board is not likely to be component of the thorough reaction strategy itself, the figure does wish to make sure that there is a strategy.
Cyber Security Consulting Company Things To Know Before You Buy
The company website value of Cyber safety has ended up being noticeable in every element because all institutions need to handle their information on the internet. As the world inclines towards an electronic makeover, where the procedures of the firms, the processing, and several such procedures take place online, the threat of the details dripping or getting hacked has increased even more.
They are investing more resources into acquiring certified personnel or incentivizing present workers to take cyber safety programs so they can remain on top of the current patterns. It implies the devices, technologies, processes, and practices that are developed to keep the data risk-free from any type of sort of assault, or damages, or unapproved accessibility.
The Main Principles Of Cyber Security Consulting Company
A cyberpunk then can input malware in their system by utilizing your name. In the next years, even more people will certainly go through cybercrimes, these consist of all the people: Who have a cellphone, Who have their checking account, That store essential documents and information on their computers, Whose name is in the straight marketing database of the firms With cybercrimes enhancing at a startling rate every day, people require to take adequate steps to shield their info or any important info they may have.
With the execution of the cyber safety and security laws, all this info can be protected. The importance of cyber safety Bonuses is not only to the services or the federal government yet small institutions too, like the education industry, the financial establishments, and so on.
The details can land in the incorrect hands as well as can become a risk to the nation (Cyber Security Consulting Company). So with the increase in the number of cyber-attacks, the organizations, particularly the ones that deal with sensitive data need to take extra measures to protect the details as well as avoid the breaching of the information.
7 Easy Facts About Cyber Security Consulting Company Explained
This way, when next you buy SSL certification, which can be of terrific assistance as it safeguards the information in between the server as well as the internet browser. Cyber Security Consulting Company. Verification and also integrity are 2 foundations on which SSL certifications stand on. To guarantee cyber security, one requires to see to it that there is control in all the components of cyber security.
